We all know about this massive Google Doc Phishing Attack that hit about 1 million accounts right?
Well this really "sophisticated attack" (really??) was based on a really spread Internet procol named OAuth. It also turns out that during the early stage of the standardization someone reported this very own attack vector but as often happens he was ignored.
Back in 2015 I also reported another "hidden feature"
of OAuth that turns an OAuth server into an open redirector that makes phishing a piece of cake.
Yesterday I was twitting about this and today I decided to imitate Eugene Pupov (lol) and work on my master thesis project. So this is the resulting mail. Have fun:
Fret not, go ahead and click and you will be redirected to:
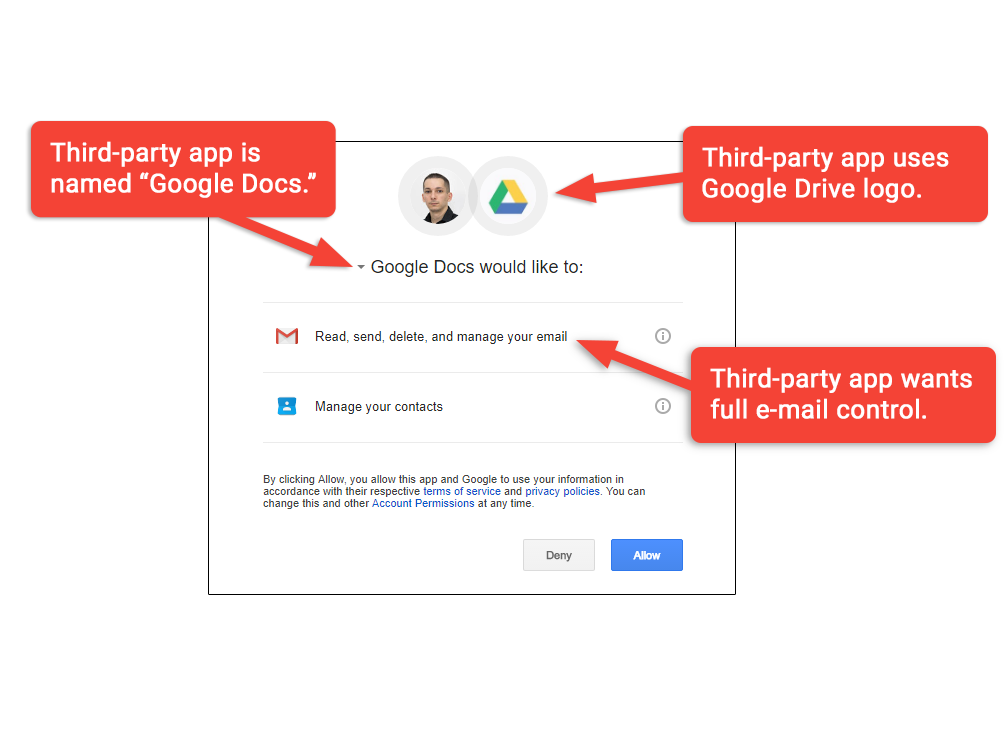 |
| Image from https://arstechnica.com/security/2017/05/dont-trust-oauth-why-the-google-docs-worm-was-so-convincing/ |
Back in 2015 I also reported another "hidden feature"
of OAuth that turns an OAuth server into an open redirector that makes phishing a piece of cake.
Yesterday I was twitting about this and today I decided to imitate Eugene Pupov (lol) and work on my master thesis project. So this is the resulting mail. Have fun:
Fret not, go ahead and click and you will be redirected to:
that is not a Github page but is rather controlled by me.
Well that's all folks. For more OAuth phishing follow me on Twitter.
P.S. for the record me and some other folks from the OAuth working group proposed a draft (3 years ago!!!) that should close this open redirector. Let's see.
P.S.2
and next patent: Method system and apparatus for use #OAuth as Phishing mechanism using isomorphic UI https://t.co/xcLtyrSom1 pic.twitter.com/FJUdBZ2xJW— Antonio Sanso (@asanso) May 4, 2017



Comments